External CA Integration
This document describes how to bring your own root certificate authority (CA) or intermediate CA into TSB to generate Istiod and workload certificates in a multi cluster Istio setup to achieve chain of trust.
When you start TSB (and thus Istio) as a demo or out of the box, the Istio instance will create its own self-signed certificate (i.e. its own root CA) to manage communication. This is convenient, but it all too commonly becomes a pain point for users who eventually start running Istio in multiple clusters. Because each Istio instance use their own root CA, they inadvertently create two islands with no trust, which leads to the clusters not being able to use secure communication.
In order to avoid this under multi-cluster Istio production setup, it is recommended that you create an intermediate signing certificate dedicated for each TSB control plane installation, per cluster. These intermediate certificates will be signed using your existing root CA private key, as well as to issue leaf certificates for the workloads deployed in the cluster. This is illustrated in the following image:
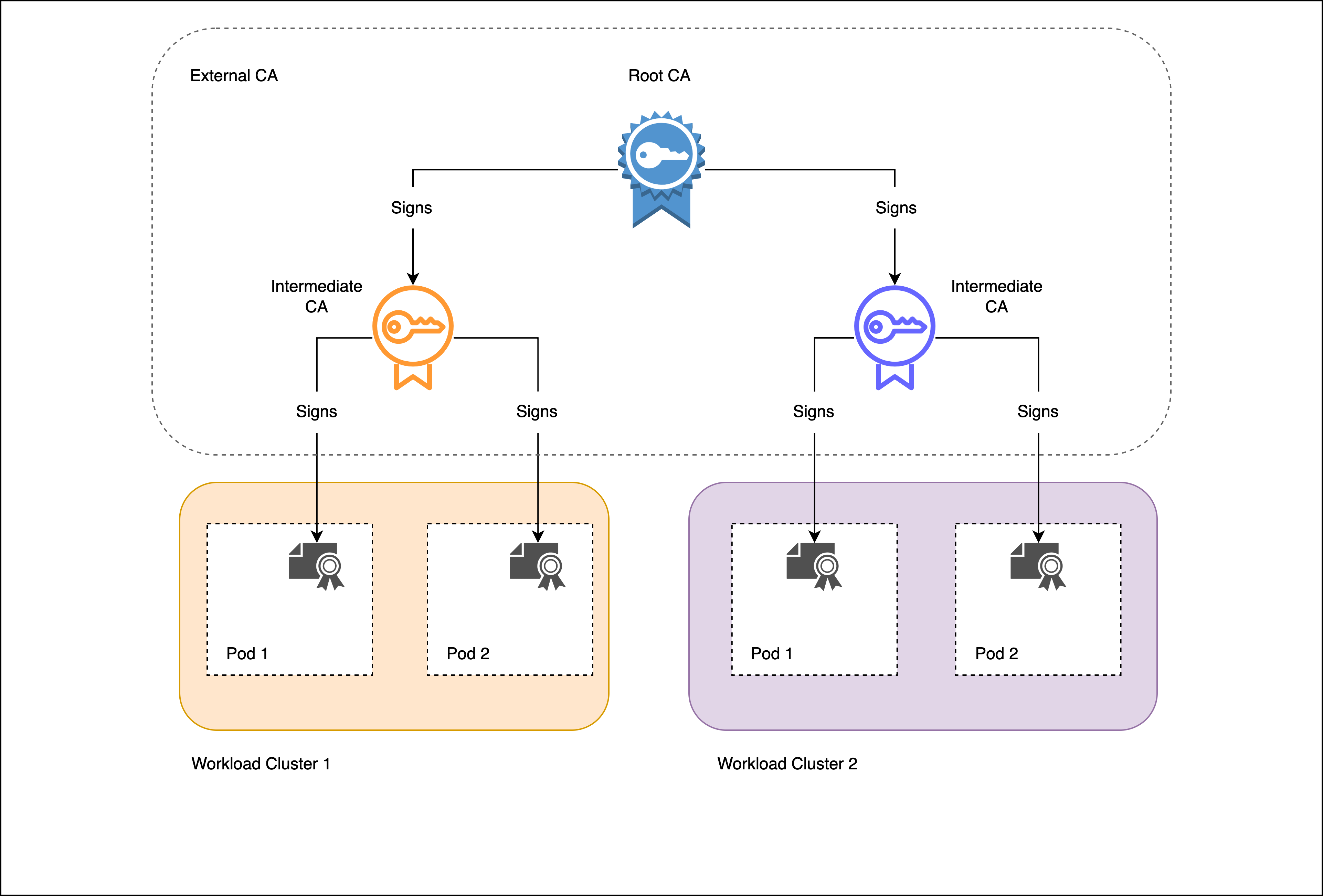
Chain of trust
If you want to learn more about chain of trust you can check "Root Istio's trust in your existing PKI" blog post from Tetrate
Before you get started, make sure you
✓ Familiarize yourself with TSB concepts
✓ Familiarize yourself with the TSB installation process. You can update existing TSB installation by updating Control Plane CR or you can do fresh installation of TSB.
✓ Familiarize yourself with Istio CSR API
✓ Install cert-manager and istio-csr
cert-manager and Istio CSR API will be used to request certificates from an external CA. After external CA authenticates and authorizes the workloads, issued certificates are provided in the response message.
cert-manager has an integration with Istio CSR called istio-csr that implements gRPC Istio certificate service. The istio-csr agent authenticates, authorizes and signs incoming certificate signing requests from Istio workloads, routing all certificate handling through the cert-manager installed in the cluster.
The rest of the document will walk you through how to integrate TSB control plane with several different types of external CAs, depending on your use case.